Windows 7 unable to connect to Wifi with WPA2-Enterprise (802.1
I have deployed WPA2-Enterprise authentication on network. Computer should use computer certificate to authenticate to Wireless network. I deployed NPS server, configured all requirements. Windows 10 didn’t have problem to connect to Wifi network. Windows 7 computers have problem.
Problem
In eventviewer (Applications and Services Logs\Microsoft\Windows\WLAN-AutoConfig) I found following error:
Network Adapter: Intel(R) Centrino(R) Advanced-N 6205
Interface GUID: {c2c428cb-76cc-4474-a043-33ce2bfe9f0d}
Local MAC Address: 60:67:20:a6:42:63
Network SSID: SECURE_WIFI
BSS Type: Infrastructure
Peer MAC Address: 34:1F:a2:AF:C8:1E
Identity: DOMAN\USER1
User: USER1
Domain: DOMAIN
Reason: Explicit Eap failure received
Error: 0x80074005
EAP Reason: 0x4005
EAP Root cause String:
EAP Error: 0x4005
Solution
Problem is very weird. When you install NPS server, NPS server will use certificate to proof of identity. By default it uses certificate created from Windows CA Template called Kerberos Authentication. This certificate has empty attribute called Subject.
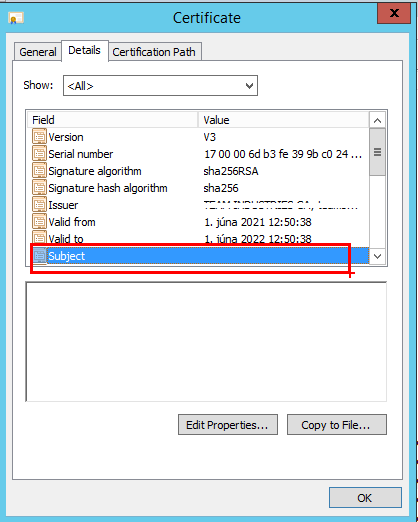
Windows 7 has problem that it doesn’t accept certificate with empty Subject attribute. Other OS’s worked fine. Solution to make it work is to populate this attribute into certificate. You can do it following way:
- Go to Certificate Template console (use MMC, add snap in –> Certificate Templates) and change template called Kerberos Authentication.
- Open properties of this template
- Go to Subject Name tab
- Change Subject name format to DNS name
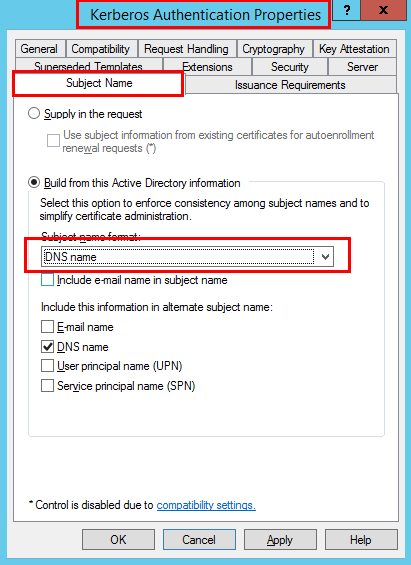
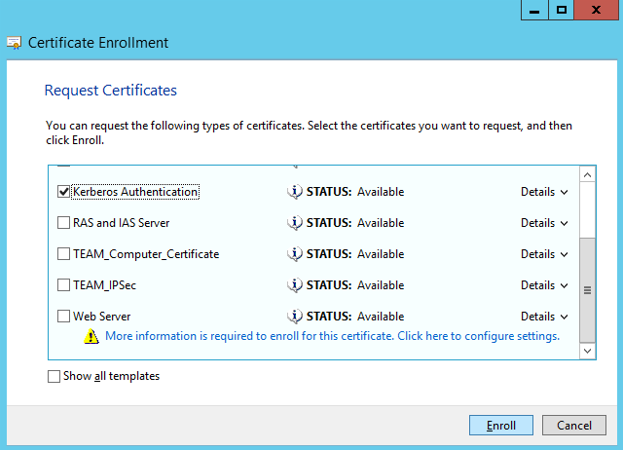
Now go to NPS server. Open the Certificates MMC (Computer), go to Personal / Certificates and right click in the details pane – All Tasks / request New Certificate. Request new certificate from template Kerberos Authentication for computer account:
After new certificate is installed under computer certification store, you can find attribute Subject populated with DNS name of NPS server:
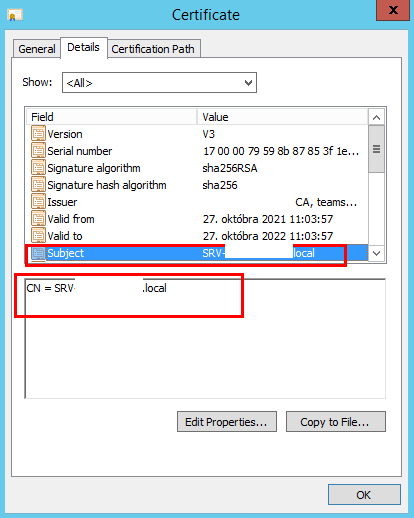
When certificate is OK, you can change certificate which should be used to proof identity.
Let’s make new certificate work on NPS server. Open NPS console. Go to Network Policies and open up your policy which handles 802.1x requests. Go to the Constraint tab, Authentication Methods / PEAP and click on Edit.
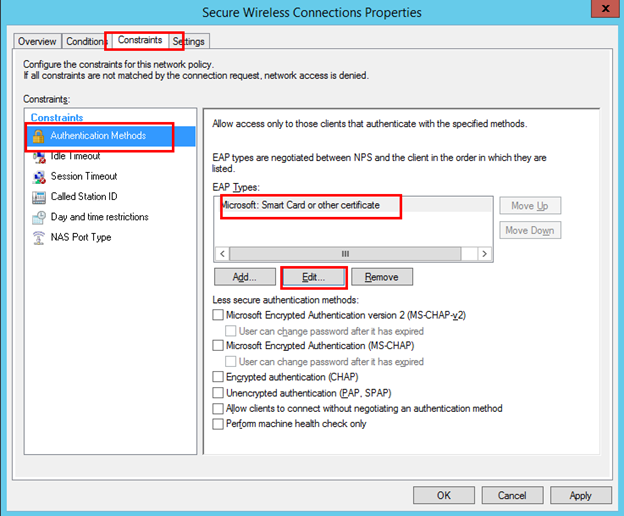
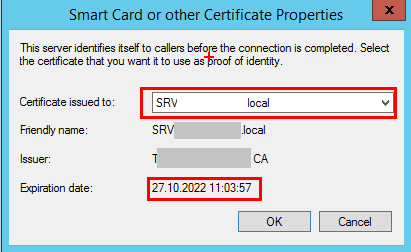
The certificate expiry date now shown should tie in to the one you just created:
Now also Windows 7 will connect to wireless network with no problem and not error event 🙂
That’s all fokls,
Recent Comments