ESET Smart Security makes problems when migrating computers between domains
I was facing weird problem with computers when I was trying to migrate computer accounts between two active directory domains. When you use ADMT to migrate computer accounts, ADMT installs ADMT Agent on computer and this ADMT Agent makes all changes during computer account migration.
Problem
When there was computer with ESET Smart Security installed I had following problems. First problem was that migration failed and in ADMT log file I received following error:
2013-04-12 16:29:54 The Active Directory Migration Tool Agent will be installed on CENTRALA.DOMAIN.LOCAL
2013-04-12 16:29:59 WRN1:0000 Could not open SCManager on \\CENTRALA.DOMAIN.LOCAL : GetLastError() returned 5
2013-04-12 16:29:59 WRN1:7015 Failed to connect to the service control manager on \\CENTRALA.DOMAIN.LOCAL, rc=5 Access is denied.
2013-04-12 16:29:59 ERR2:7006 Failed to install agent on \\CENTRALA.DOMAIN.LOCAL, rc=5 Access is denied.
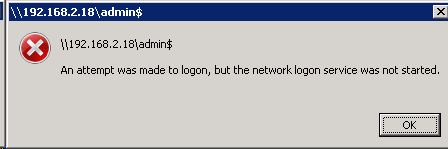
So error number 5 means I have no rights somewhere. After reading couple pages of ADMT documentation I found out that ADMT installs ADMT Agent using Admin share called ADMIN$. So I tried to access ADMIN$ share on computer CENTRALA.DOMAIN.LOCAL. I received following error:
I have never seen such an error:”An attempt was made to logon, but the network logon service was not started.”. I checked services on computer CENTRALA.DOMAIN.LOCAL and Windows was right. Service NETLOGON was Disabled!
Solution
I had to temporary turn off ESET Smart Security (I would preffer not use this software at all 🙂 ) and also enable and start service NETLOGON.
Conclusion
Every computer I migrated and had installed ESET Smart Security had the same problems. So IMHO ESET Smart Security has changed service NETLOGON to Disabled. I really don’t understand why this is necessary, but I think it’s not right way “smart security product” should protect your computer.
I found one article about disabling NETLOGON service as security practice. It’s maybe good security practice, but there is also pitfall stated on websie:
If you disable the NetLogon service, a workstation no longer functions reliably as a domain member. This setting may be appropriate for some computers that do not participate in domains. However, it should be carefully evaluated before deployment.
I’m wondering what other functions are not available when NETLOGON disabled (besides not accessible ADMIN$ share) on domain member computer.
I hope this helps someone 🙂
Recent Comments