How to track deleted files
I am often asked to restore files on fileservers and also look for user who deleted files. By default there is no auditing for files enabled on fileservers. I will write how I do enable it and how it works for me.
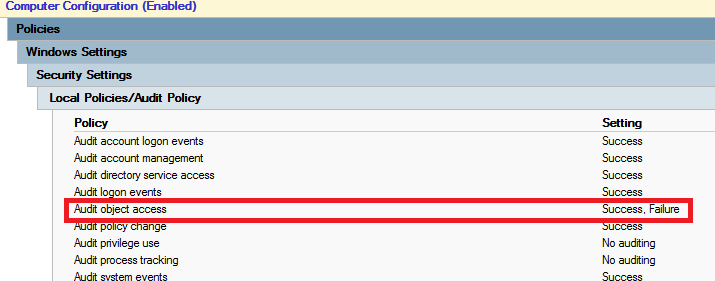
First of all you need to enable audit policy Audit object access. This audit policy handles auditing for files, registry keys, shares, … To enable this audit policy you need to set it in GPO Computer Configuration – Policies – Windows Settings – Security Settings – Local Policies – Audit Policy – Audit object access and set it to Success, Failure.
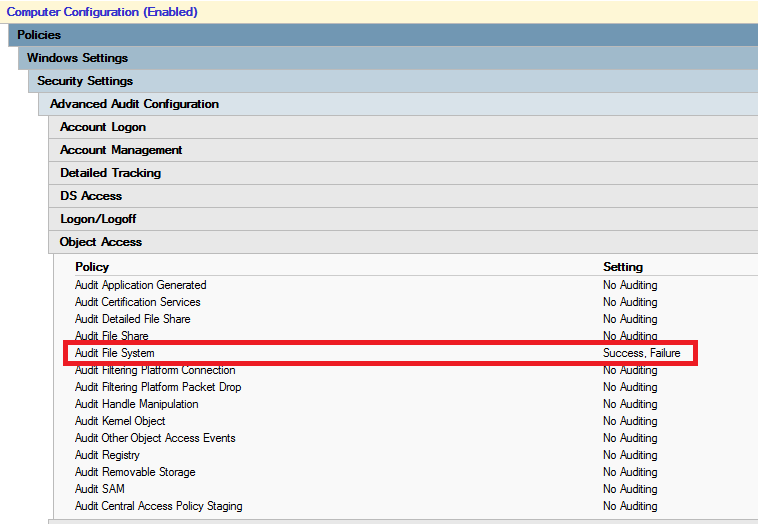
This audit policy enables auditing for lots of objects to audit. I want to audit only File System. To find out what audit policy settings are applied on computer use following commnad auditpol.exe /get /category:*. To enable only wanted auditing I have dumped settings using auditpol.exe command and set same auditing in GPO, but under Object Access I just enabled File System auditing. You can set this settings under Computer Configuration – Policies – Windows Settings – Security Settings – Advanced Audit Configuration.
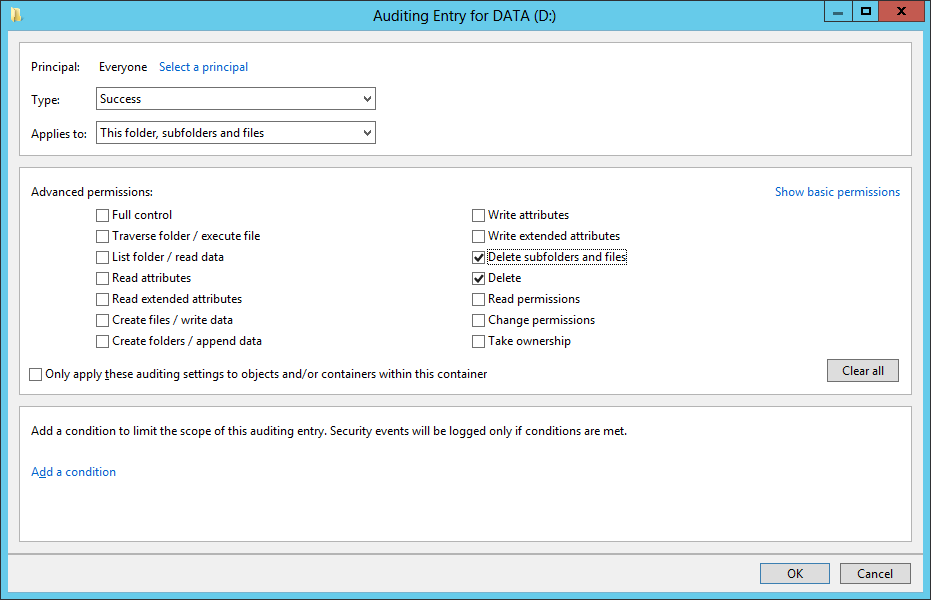
Now you need to setup Auditing on whole Disks or Folders:
When these settings in GPOs are applied there are new events in security event log. We need to look for event number 4659 and make some reporting out of it. I’ve created powershell script which I run every day right after midnight and it creates HTML report and also CSV files which can be used in some powershell manipulation. Here is a powershell script:
#
# Get-DeletedFileLog
# This function gets events 4659 about delted files and generate HTML reports
#
#
# Declaration
#
[datetime]$Yesterday = ((Get-Date) - (New-TimeSpan -Day 1)).date
[datetime]$Today = (Get-Date).date
[int]$EventID = 4659
[string]$Path = "D:\Logs\Deleted Files"
[int]$Limit = (Get-Date).AddDays(-180)
Try
{
#
# Get events from security eventlog
#
[array]$EventList = Get-WinEvent -FilterHashtable @{Logname='Security';Id=$EventID;StartTime=$Yesterday} -Oldest -ErrorAction Stop
#
# Extend Event by XML data fields
#
foreach ($Event in $EventList)
{
$EventXML = [xml]$Event.ToXML()
For ($i=0; $i -lt $eventXML.Event.EventData.Data.Count; $i++)
{
Add-Member -InputObject $Event -MemberType NoteProperty -Force -Name DateFileDeleted -Value $Event.TimeCreated
Add-Member -InputObject $Event -MemberType NoteProperty -Force -Name UserName -Value $EventXML.Event.EventData.Data[1].'#text'
Add-Member -InputObject $Event -MemberType NoteProperty -Force -Name DeletedFile -Value $EventXML.Event.EventData.Data[6].'#text'
}
}
#
# Generate HTML report
#
$EventList | Select DateFileDeleted, UserName, DeletedFile | ConvertTo-Html | Out-File "$($path)\$($Today.Year)$($today.Month)$($Yesterday.Day)_DeletedFiles.html"
$EventList | Select DateFileDeleted, UserName, DeletedFile | ConvertTo-Csv | Out-File "$($path)\$($Today.Year)$($today.Month)$($Yesterday.Day)_DeletedFiles.csv"
}
Catch
{
# If there is a problem
Write-Host "No events $EventID to record."
}
#
# Remove old reports
#
Get-ChildItem -Path $Path -Recurse -Force | Where-Object { !$_.PSIsContainer -and $_.CreationTime -lt $Limit } | Remove-Item -Force
# EOF
This script also cleans up files older than 180 days. In HTML file you can see when, who and what deleted. I didn’t excluded files started with “~”, which are also known as temporary Office files, which are created during opening Office documents. This is because now I know who opened which files and when.
Enjoy,
Recent Comments