Sometimes when you work on linux in bash you don’t want to leave commands in bash history (.bash_history). Easy way to clean it up it’s to run following command:
HISTSIZE=0
Now your bash history will be not accessible and not saved when you logoff.
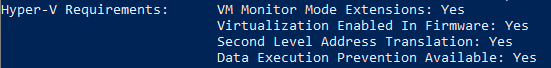
If you want to know if your computer is ready to host Hyper-V role you can check it quickly using old command systeminfo.exe with new feature. This new feature is in systeminfo.exe which is included in Windows 8 and higher and Windows Server 2012 and higher.
When you run it you can see the last output lines about Hyper-v Requirements:
That’s all for today,
I just found one cool utility. It’s called clip.exe. You can use this utility to input the content from pipline into clipboard and then paste the content of clipboard where ever you want.
Here a example:
ipconfig /all | clip
When you run this all the output from command “ipconfig /all” is stored into windows clipboard. Now you can Paste (CTRL+V) this into any application you want.
When you want to read the content of any file into windows clipboard you can use following command:
clip < C:\kukuc.txt
This cool utility came with Windows Server 2003 (not in Windows XP) and stayed there until Windows 8 and Windows Server 2012 R2.
Have a good day,
I’m creating couple powershell scripts which I use in my work. I want to share couple of them with you. So here is a script which look for domain computers and then check who is logged on those online machines.
$ADSearchBase = "OU=Computers,DC=domain,DC=local"
$ADFilter = "*"
Function Get-LoggedUsersOnComputers
{
$ADComputersList = Get-ADComputer -SearchBase $ADSearchBase -Filter $ADFilter
foreach ($ADComputer in $ADComputersList)
{
Write-Output $ADComputer.Name
Try
{
$ExplorerProcesses = Get-WmiObject -ComputerName $ADComputer.Name -Class win32_process -Filter "Name='explorer.exe'" -ErrorAction Stop
}
Finally
{
If ($?)
{
foreach ($ExplorerProcess in $ExplorerProcesses)
{
Write-Output " $($ExplorerProcess.GetOwner().User)"
}
}
Else
{
Write-Output " <<< Could not connect"
}
}
}
}
Get-LoggedUsersOnComputers
If you have any remark on my script, please, let me know. I will be happy to make it more cute 🙂
I was playing today with new feature called PowerShell Web Access. This feature was brought in Windows Server 2012. It is very easy to install and easy to use. You need to select one server which will act as Web Access PowerShell gateway server. You will be connecting to this server using SSL and this server will use PowerShell remoting to access computers inside your network. So let’s make it work.
First you need to run PowerShell as a admin on gateway server:
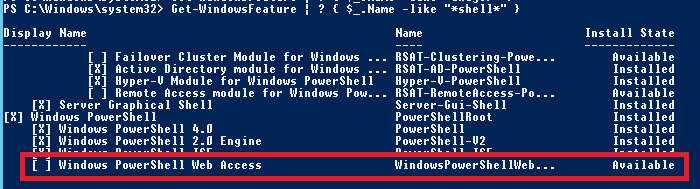
Let’s look for Windows features which contain word “shell”:
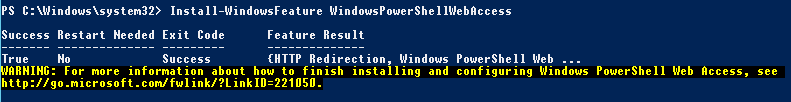
Windows PowerShell Web Access is the feature we want to install. So let’s install it:
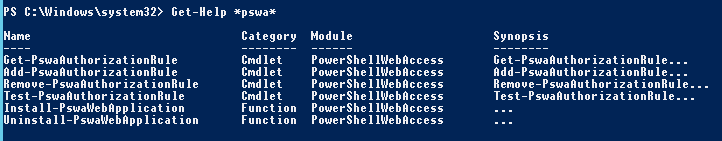
Now we can look at this website to lear more, but let’s play more. Now we have new cmdlets containig word “pswa” (PowerShell Web Access):
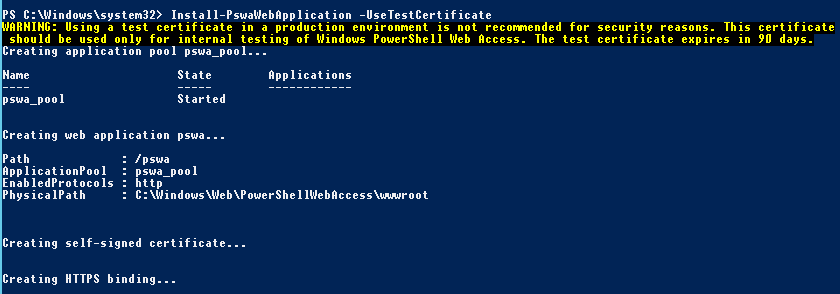
We installed pswa feature, but this feature didn’t install its web component into the server. So let’s install pswa Web application using cmdlet Install-PswaWebApplication with parameter -UseTestCertificate. This parameter creates self-signed SSL certificate for this new site, you can use your own certificate. Be aware that this certificate expires in 90 days.
New website was created:
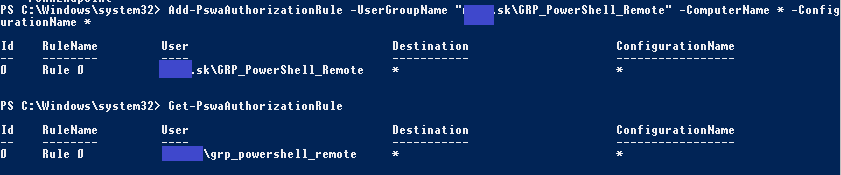
By default no one can use Powershell access gateway. You need to define explicit rules who, where and what can do. For easy test you can use following rule for domain group called GRP_PowerShell_Remote to access all computers with all permissions:
Now everything is prepared. We need to make some changes in network (routers and NAT) to be able to access 443 port on server from Internet. Now when we open site, we can see:
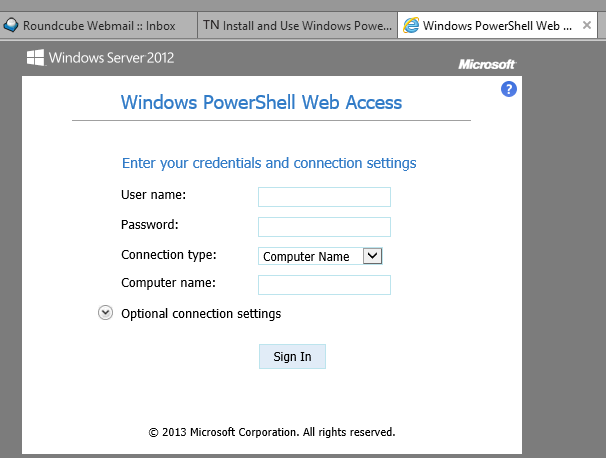
And now you can work on machines inside your network. It’s secure and reliable:
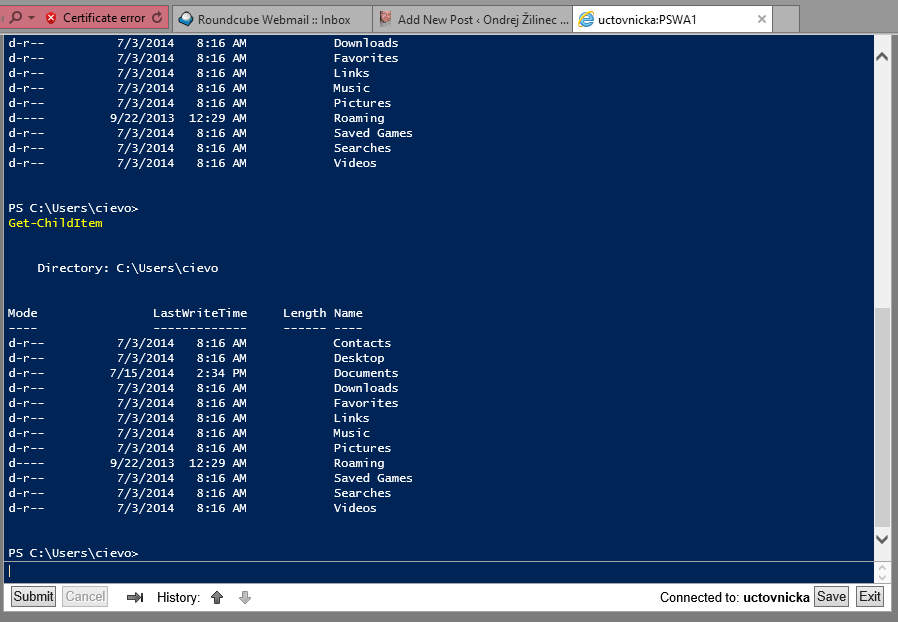
This is very nice and cute feature.
I hope you will start to use and enjoy it.
Have a nice day.










Recent Comments