What’s new in WSUS in Windows Server 2012
Installation of WSUS on Windows Server 2012
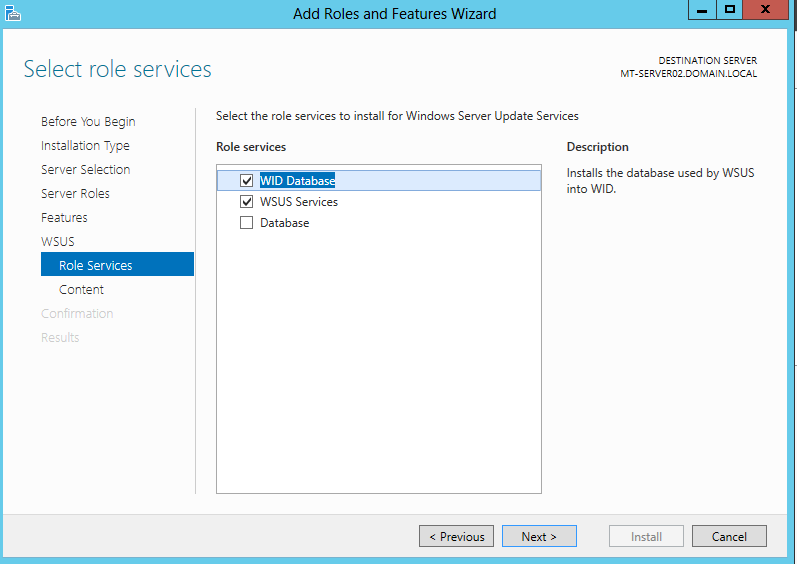
I started to install WSUS service on Windows Server 2012. I selected to install Windows Internal Database as store of WSUS metadata.
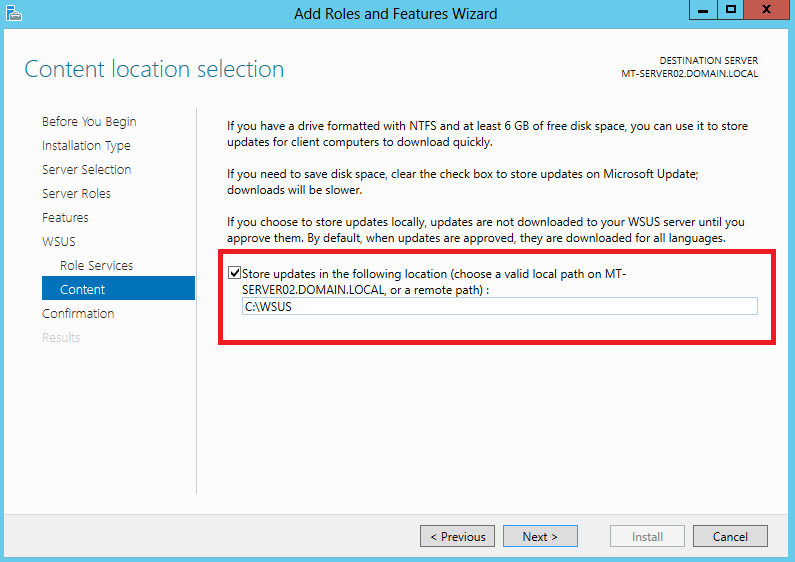
I selected to store updates on local C:\ drive (it’s just testing machine):
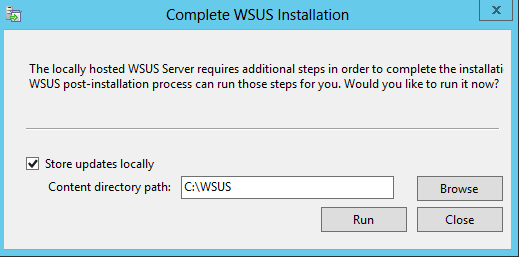
After first run on Windows Server Update Services management tool WSUS asks again if I want to store updates locally or not:
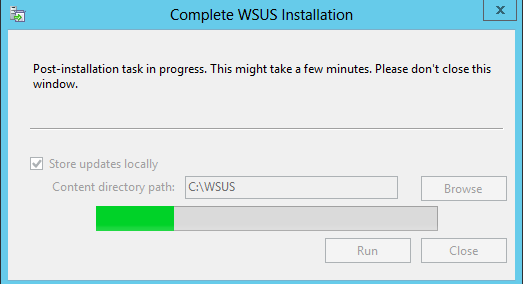
When I click Run, post-installation starts to run:
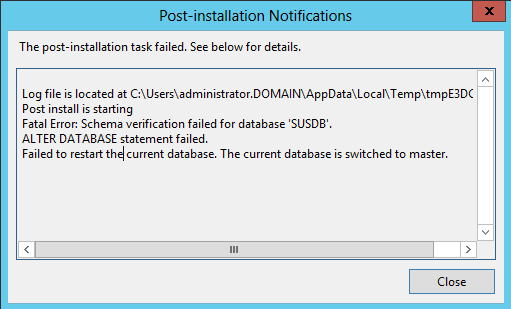
And I received Post-installation “notification” 🙂 in Microsoft word it means I have a problem (Failed to restart the current database. The currecnt database is switched to master):
So if computer has problem with restarting database, let’s restart service. Didn’t help 🙂 Let’s restart whole computer. Didn’t help either. So the problem will be somewhere else.
I tried to install WSUS from scratch. I uninstalled WSUS and also Windows Internal Database feature. I also deleted data for Windows Internal Database from directory C:\Windows\WID. Then I installed WSUS with all dependecies – WID, IIS, …
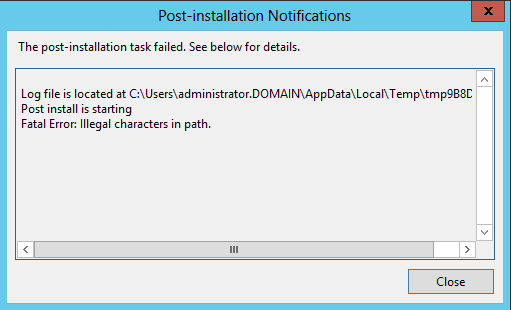
Now I’m getting different error:
Problem was backslash in input window for defining directory to store updates 😀 This path was predefined by wizard and it was wrong. This is really funny 🙂
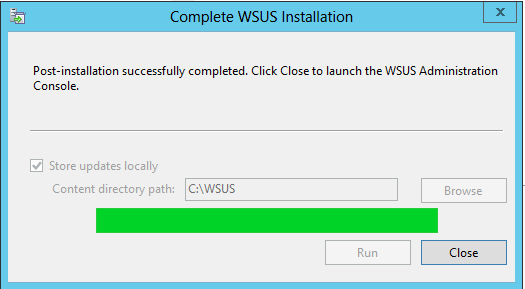
So after reinstallation of WSUS and WID and defining “correct” path to update store directory (without backslash on the end 🙂 ) everything looks to be done correctly:
Let click Close and look what’s new in WSUS. First we need to configure WSUS and I did it using WSUS Wizard. I don’t see any news in this Wizard compared to older one.
Exploring WSUS
I haven’t notice any news in WSUS mmc console. I always use client side group targeting. This feature allows you to create groups of computers in WSUS structure. It can be used to target updates specified for testing to just group of computers and so on. To make this working you need to set client side of group targeting by defining name of Group and also you need to create new Computer Group in WSUS structure. What I always forget it to create these Computer Groups in WSUS structure 🙂 I would love to see some option to allow WSUS to create these Computer Groups automatically. But this didn’t happend of this version of WSUS.
I think the most powerful thing Microsoft added into WSUS is support for Powershell cmd-lets. Most of the time WSUS settings about update Classifications and update Products are same from customer to cutosmer, so you can automate this settings using cmd-lets Get-WsusClassification, Set-WsusClassification, Get-WsusProduct and Set-WsusProduct.
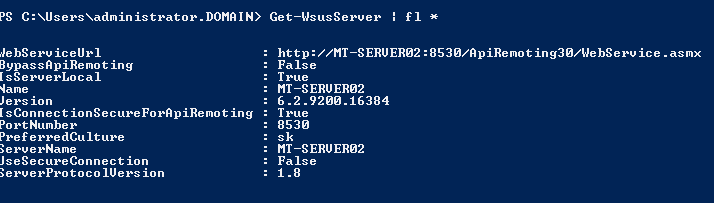
To get some information about WSUS Server it selft you can use cmd-let Get-WsusServer:
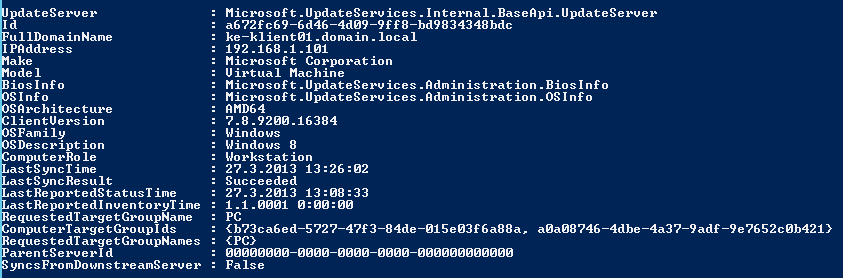
There are more interesting cmd-lets. One is Get-WsusComputer which prints out some more information about computer reported into WSUS:
Get-WsusComputer has lot of ability to filter out computers on some conditions. Failed, Needed, …
To manage updates from powershell you can use cmd-lets Get-WsusUpdate, Approve-WsusUpdate and Deny-WsusUpdate. You can for example approve all updates that are Unapproved and FailedOrNeeded:
Get-WsusUpdate -Classification All -Approval Unapproved -Status FailedOrNeeded | Approve-WsusUpdate -Action Install -TargetGroupName “All Computers”
And the last cmd-let I really love, because I can make scheduled task to run Clean-up Wizard. Cmd-let is Invoke-WsusServerCleanup. You can do every cleanup task you can make from GUI.
Conclusion
I don’t think there is too much to improve on WSUS, but little powershell support for WSUS is handy.
Recent Comments