Reset Computer accounts in Active Directory domain
One of our customer migrated his whole IT infrastructure into another datacenter. We powered off virtual machines at production site and powered on cloned versions of virtual machines. Domain Controllers were up all the time. Only member servers’ clones moved into another datacenter. They’ve ran for three days in another datacenter. Active Directory domain was up all the time. After tests we deleted clones in another datacenter and powered on virtual server in primary datacenter – their friday’s copies. And now we had problems on couple of servers.
During those three days couple of server changes their passwords in domain. When we powered on friday copy of virtual machine, it tried to authentificate in domain with password which was valid on Friday, but it was going to expire within three days. This means that password from Friday were not valid on Sunday 🙂 – logical. When we powered on those affected machine we saw following errors:
- Event 3210
- Event 5721
- Event 5722
- We couldn’t log in into domain on those servers – only local admins worked
- Message when logging into domain: “Windows cannot connect to the domain, either because the domain controller is down or otherwise unavailable, or because your computer account was not found. Please try again later. If this message continues to appear, contact your system administrator for assistance.”
- Message when logging into domain:”The security database on the server does not have a computer account for this workstation trust relationships.”
- Network on server is marked as Unauthenticated
Why did this happend?
Every computer in domain has its own domain account. It’s domain account which is similar tu users’s accounts. Every computer has its own password into domain. It uses this account and password to authentificate into domain (services running under SYSTEM service and Network Service). Computer accounts also reset their passwords for security reason. By default they reset their password every 30 days. You can configure this by registry or by GPO policy settings
Registry
HKLM\SYSTEM\CurrentControlSet\Services\NetLogon\Parameters
DisablePasswordChange (default off) prevents the client computer from changing its computer account password. To disable, give it a value of 1.
MaximumPasswordAge (default 30 days) determines when the computer password needs to be changed. Change it to whatever number of days you think may be enough.
GPO Policy
Computer Configuration\windows Settings\Security settings\Local Policies\Security Options
Domain member: Disable machine account Password changes
Domain member: Maximum machine account Password age
This problem can occure also when you use image backups (for example VCB, Ghost,…) and you restore machine with old password. Or you use snapshot technologies such a VMWare snapshoting and you revert back to snapshot with old password.
Changing this settings is very extensive published as a Best-practice when you use image backup or snapshot solutions, but it not very secure to do it this way. Better solution is comming, hold on 🙂
Solution
This problem was solved in our case by re-joining computer in domain. But here we didn’t know if applications and services on computers would work after rejoining domain. They worked (for example MSSQL).
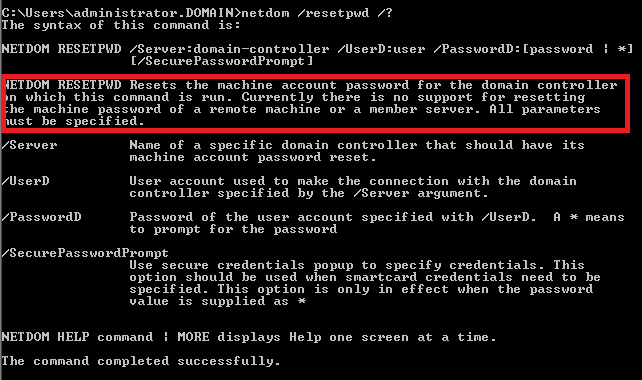
I contacted also my friend MVP Ondrej Sevecek (www.sevecek.com) who gave me a another, better, solution for this problem. You need to log into computer under account which has local admin rights. Then you can use command:
NETDOM RESETPWD /Server:SRVDC01 /UserD:domain\zilinec_admin /PasswordD:Heslo123
- /Server:SRVDC01 – this is domain controller towards which you will be reseting password
- /UserD:domain\zilinec_admin – domain account with domain admin rights
- /PasswordD:Heslo123 – password for account specified in /UserD parameter
Here is how it looks in practice
I’ve created domain called domain.local (smart, eh? :-)) and created one domain controler (SRVDC01) and computer as a member server (SRVXX01).
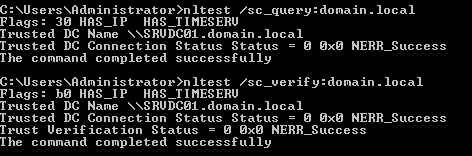
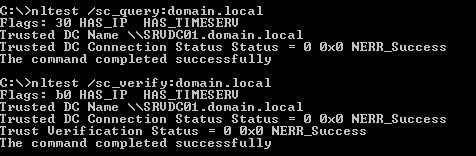
When I check if secure channel between domain controller and member server is in good condition we will run:
Now I changed password for computer account on domain controller. After restart of server SRVXX01 I see on domain controllers following security events:
An account failed to log on.
Subject:
Security ID: NULL SID
Account Name: –
Account Domain: –
Logon ID: 0x0
Logon Type: 3
Account For Which Logon Failed:
Security ID: NULL SID
Account Name: SRVXX01$
Account Domain: DOMAIN
Failure Information:
Failure Reason: Unknown user name or bad password.
Status: 0xc000006d
Sub Status: 0xc000006a
Process Information:
Caller Process ID: 0x0
Caller Process Name: –
Network Information:
Workstation Name: SRVXX01
Source Network Address: 192.168.47.128
Source Port: 49414
Detailed Authentication Information:
Logon Process: NtLmSsp
Authentication Package: NTLM
Transited Services: –
Package Name (NTLM only): –
Key Length: 0
This event is generated when a logon request fails. It is generated on the computer where access was attempted.
The Subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The Logon Type field indicates the kind of logon that was requested. The most common types are 2 (interactive) and 3 (network).
The Process Information fields indicate which account and process on the system requested the logon.
The Network Information fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
– Transited services indicate which intermediate services have participated in this logon request.
– Package name indicates which sub-protocol was used among the NTLM protocols.
– Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
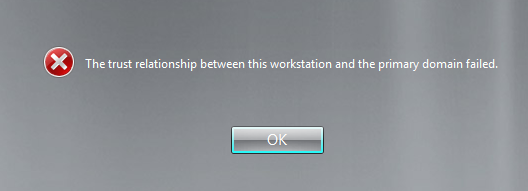
When I try to log into machine with domain account I get:
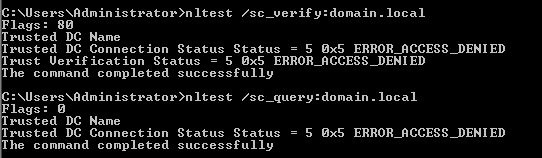
After loggin with local admin I tried nltest utility and I get following error:
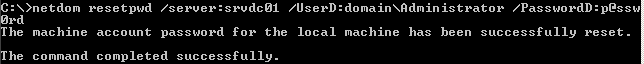
I will not rejoin computer to domain. Let’s run our magic command:
Let’s have a look if nltest.exe will give us good result:
And I can even log into machine with domain account without restart! What a great help! 🙂
I really DO like Microsoft, but when you check help for command netdom /resetpwd you see Microsoft stating that this is not solution for memeber servers, it’s just for domain controllers. It’s not truth!!! When I was debugging problem I skipped this step because of help I read:
So THANK YOU MICROSOFT FOR NOT PROVIDING US GOOD HELP 🙂
Ondrej Sevecek also wrote blog in more details about this issue at http://www.sevecek.com/Lists/Posts/Post.aspx?ID=103.
My big thanks for Ondrej Sevecek for a help he provided 🙂
Thanks for the good article. I really didn’t want to rejoin to the Domain as nothing changed on my machine.
Cheers,
thanks for this article so how do you do this for the Windows 7 powershell since it does not come with netdom? I know you can install RSAT but it’s too complicated.
Windows 7 doesn’t come with NETDOM utility. You are right, you need to install it by installing RSAT (http://www.microsoft.com/en-us/download/details.aspx?id=7887) and then enabling feature from RSAT by:
– going to Control Panel -> Programs and Features -> Turn Windows features on or off
– in the treeview, go to Remote Server Administration Tools -> Role Administration Tools -> AD DS and AD LDS Tools and select AD DS Tools. Click OK.
Thanks mate for this article! Sick of broken trusts between clients and domains!
You can use netdom.exe and netdom.exe.mui and copy it to other machines without installing RSAT.
Doesn’t have to go into where you grabbed the files from as long as the structure looks similar to
how it is in system directory.
This below works just fine, as long as you are calling the utility from “C:\netdom\”
c:\Netdom\netdom.exe
c:\Netdom\en-US\netdom.exe.mui
Once again, thanks mate.
Thank you!
Thank you, great post. No restart required!
You are welcome and I’m happy I could help.
This is awesome… I was encountering this issue after swapping the hard drive from a faulty desktop to another desktop of the same model. Thanks for this post…
Happy to help.
Great article.
Must say it was a joy not to fix this issue using the Remove/Add method.
@Riaan
Happy to read 🙂
Hi all,
I already try but i get failed as below message:
The machine account password for the local machine could not be reset.
No mapping between account names and security IDs was done.
The command failed to complete successfully.
BR,
Khem
@Khemarin
Do you have existing account in domain for your computer? I quess it’s missing.
Unfortunately,
This doesn’t work if you only have a single DC with no backup DC. 🙁
Actually, in case anybody else finds this, and ONLY has a single DC, do the following:
Stop the KDC Service, then run the above command but replace /server:OtherDomain with /server:LocalServerIP .
This succeeded for me, and now my DC is back up and running.
@Oliver
Thank you for you reply. Question is why you have only single DC. It’s way to hell 🙂
Thank you, very well post
Purely because I run it at home, and having two DC’s isn’t feasible..
Those are examples I was looking for. Helpful for me. Thank you.
@Hubert Trzewik
Happy to help.